Opera 73.0.3827.0 developer update
-
padua last edited by
@leocg Obviously, of course!
Well, at least, it should be so in a thoroughly QA'd update process.
The issue here is that there is a difference, in this situation - the automatic update throws a warning and the downloaded update (according to other posters) does not.
My request "Can we request some one on the dev / QA team to see what the difference is between an autoupdated update and downloaded update" was for them to look into this specific case and not a request for general info on autoupdate vs downloaded update.
Thanks again to everyone in the Opera browser team for a good browser - just that this issue needs to be escalated for a QA team / dev team response.
-
gmiazga Opera last edited by
Hey, we are currently looking into the issue with Windows Defender detecting .dll. All our Windows binaries before being published are scanned on VirusTotal. Version 73.0.3827.0 still shows no detections and binaries uploaded there are same like the ones on our autoupdate servers (few CDNs I checked at least) and FTP server.
-
andrew84 last edited by
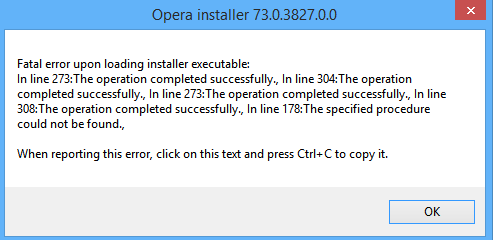
I can confirm the same on Win 8.1x64,
Kaspersksy doesn't detect it, but I turned it off and activated Windows Defender. After running the installer I've got the same result.
-
ziegensatan last edited by
@gmiazga are there any news? if it is a false positive, it should be reported to microsoft
https://docs.microsoft.com/de-de/windows/security/threat-protection/microsoft-defender-antivirus/antivirus-false-positives-negatives -
A Former User last edited by
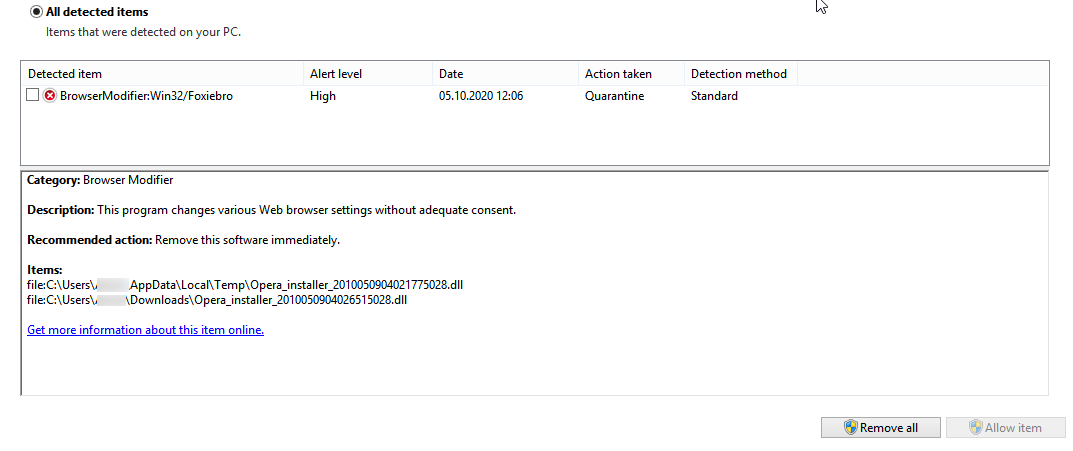
@gmiazga: The problem is that Opera was trying, insistently, to download these .dll files identified as threats by Windows Defender. In fact, I was prevented from uninstalling Opera by the conventional method.
-
AndrewMills last edited by
Hi, in my new installation, every time I start Opera developer, Windows antivirus warns of a serious threat and appear this message...
https://ibb.co/zR3V45v -
burnout426 Volunteer last edited by
@gmiazga FWIW worth, I also submitted the dll for review as a false positive (and explained the situation and linked to threads about it) to Microsoft. See https://www.reddit.com/r/operabrowser/comments/j4ihvn/foxie_malware/g7ubuqi/?utm_source=reddit&utm_medium=web2x&context=3 for their response. Hopefully you have better luck.
-
burnout426 Volunteer last edited by
@kened said in Opera 73.0.3827.0 developer update:
In fact, I was prevented from uninstalling Opera by the conventional method.
In https://www.reddit.com/r/operabrowser/comments/j4ihvn/foxie_malware/g7s2mqv/?utm_source=reddit&utm_medium=web2x&context=3, I mentino how I had to kill some Opera processes to do some cleanup to get updating working again. I also had to do that to be able to uninstall Opera.
-
A Former User last edited by
@burnout426: I think we deserve a full explanation about what is happening. This is not normal.
-
burnout426 Volunteer last edited by burnout426
@kened What I know right now is that Windows Defender doesn't think it's malware or a virus. It just tags it as a potentially unwanted program. It's detected as BrowserModifier:Win32/Foxiebro. I can understand that as the Opera installer actions can and do modify Opera. So, it is indeed a "BrowserModifier", technically. The weird thing is it just started happening recently. I'm not sure if it's due to a definition update for Windows Defender where they have stricter rules or just a change (it'd be a safe change) in Opera's installer actions that triggers Defender now. And, remember. No other anti-virus does this.
If you're sure you don't have any real BrowserModifier:Win32/Foxiebro infections on your computer, you can allow the threat in Windows Defender until this gets sorted.
Reading the "Unwanted Software" section at https://docs.microsoft.com/en-us/windows/security/threat-protection/intelligence/criteria leads me to believe that Defender wants something in Opera's installer to be user-initiated in some way. Opera might just have to change something with one of its installer functions (when checking/doing updates etc.) to work around the detection and make Defender happy. But, we'll have to wait and see what Opera says.
-
A Former User last edited by
@leocg: I think it's a little more complicated than that.
I repeat: I was unable to uninstall Opera Developer. I had to remove all folders related to it. But I really hope it was just a false positive. -
A Former User last edited by
@leocg: Probably, in the next few hours we will have a new build. We'll know better what's happening.
-
gmiazga Opera last edited by
Microsoft removed this detection. Their full reply:
We have removed the detection. Please follow the steps below to clear cached detection and obtain the latest malware definitions.
- Open command prompt as administrator and change directory to c:\Program Files\Windows Defender
- Run “MpCmdRun.exe -removedefinitions -dynamicsignatures”
- Run "MpCmdRun.exe -SignatureUpdate"
Alternatively, the latest definition is available for download here: https://www.microsoft.com/en-us/wdsi/definitions
From our side there have been small changes in installer code on developer which probably got detected as malware together with Microsoft definitions update done on 2-3 October.