Meltdown & Spectre the last Opera 68.0.3618.104 vulnerability
-
A Former User last edited by
@anastasia-mx To be honest, I don’t know. I checked Opera Stable, Beta, Dev and Chrome Canary 84.
Everywhere the same. "Your browser is NOT VULNERABLE to Spectre" -
anastasia-mx last edited by
@johnd78
probably a bug. are there any other sites to check for vulnerabilities? -
leocg Moderator Volunteer last edited by
@anastasia-mx Probably a false positive.
Did you check with a clean profile? -
A Former User last edited by
@anastasia-mx
This Chinese test is very old, I have not seen others. In Opera, this vulnerability was closed in version 51 in 2018: DNA-66724 “Spectre” vulnerability check fails in Opera 51 & 52 -
donq last edited by
This vulnerability may depend on CPU make and model, BIOS version, OS version etc etc. On my PC it says 'vulnerable' - I have quite old system, not lately updated OS and so on

-
anastasia-mx last edited by
@donq the system is new, all patches are worth it. I’m just using another Firefox browser - everything is fine with me, there is no vulnerability.
-
donq last edited by donq
@anastasia-mx
What offline scanner says? https://www.grc.com/inspectre.htmFor my PC/OS it says so, thereby Opera reporting same is no wonder:
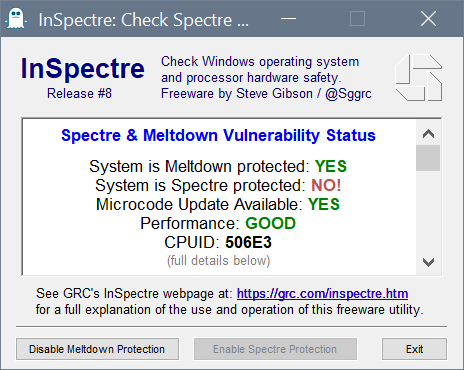
There are more tools listed: https://www.neowin.net/forum/topic/1353430-inspectre-grccom-spectre-meltdown-testing-tool/
-
burnout426 Volunteer last edited by burnout426
For me, with 2nd-gen Intel Core i5, https://xlab.tencent.com/special/spectre/spectre_check.html says I'm vulnerable to Spectre in all browsers except Firefox. All the other browsers I tested are Chromium-based. I tested in Opera 67 and 66 too. They show the same thing.
With https://www.grc.com/inspectre.htm, it says I'm protected for both Meltdown and Spectre. It says a microcode update is available. Performance is "Slower" due to the workarounds.
I'm on Windows 10 OS Version 1909 (Build 18363.836).
-
andrew84 last edited by andrew84
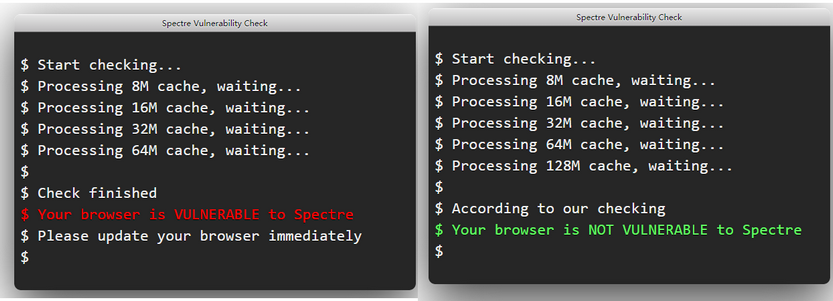
O58 - 58.0.3135.132 (I don't see 'processing cache' for some reason)
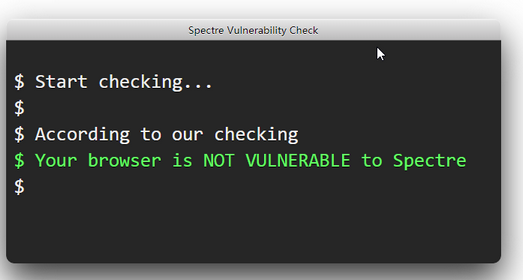
68.0.3618.104
random result (when I click 'recheck'), sometimes it checks only few caches (8, 16, 32), sometimes checks all caches until 128. When it includes all caches including 128 it shows NOT vulnerable. if less caches were checked, then it shows vulnerable. Win 8.1 3rd gen core i3.
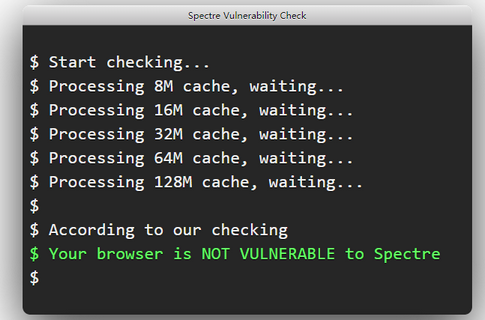
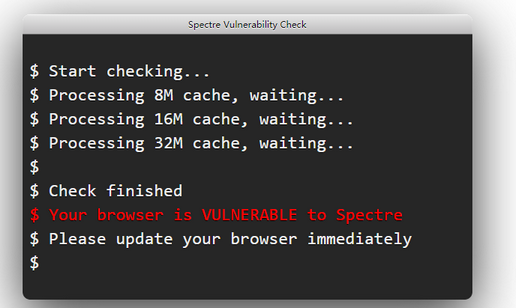
-
andrew84 last edited by andrew84
I have the same in latest MS Edge build (Canary), if 128 cache was scanned, then all is fine.
-
anastasia-mx last edited by
@leocg said in & Spectre the last Opera 68.0.3618.104 vulnerability:
Did you check with a clean profile?
if you delete all the settings, it will be very bad and I will need to configure a lot from the beginning
@donq said in & Spectre the last Opera 68.0.3618.104 vulnerability:
What offline scanner says? https://www.grc.com/inspectre.htm
Meltdown & Spectre - NO!, NO! updates strongly slow down the system, I do not want to put them, I have hope for the browser itself.
@leocg said in & Spectre the last Opera 68.0.3618.104 vulnerability:
What about other Chromium based browsers?
not used by others Chromium based browsers. I only use Mozilla - everything is fine in it, there is no vulnerability.
any other sites to check for vulnerabilities?
-
leocg Moderator Volunteer last edited by
@anastasia-mx Since Opera is a Chromium based browser, you need to also check with other Chromium based browsers to have a valid comparasion.
-
leocg Moderator Volunteer last edited by
@anastasia-mx A clean profile would help checking if the problem is not being caused by a broken profile.
-
donq last edited by
IIRC at least some (theoretical) browser attacks were based on precision timing in javascript and mitigation was done by randomizing JS timing errors - all such behavior is seated deep inside JS engine and should not be related to broken profile. Well, there likely are some JS flags, which may alter engine behavior - and you may search or ask on chrome/chromium forums, have they changed anything related to spectre or JS timings.
I have not heard about (widespread) real-word exploits, based on spectre (or meltdown). I would think such kind of vulnerabilites can be used for targeted attaks, where every bit of information can be valuable; for generic attakcs (to take PC over) this is a bit hard and unpredictable to use - of course I may be wrong here.
-
A Former User last edited by
I found a blog comment from the Opera developers. https://blogs.opera.com/desktop/2018/01/opera-50-0-2762-67-stable-update/
-
A Former User last edited by
@leocg I meant the developers' blog comments on this issue. As far as I remember, when a problem with this vulnerability appeared, the developers forcedly disabled
opera://flags/#shared-array-bufferflag. Now this flag is gone.