Kill-Switch Feature
-
A Former User last edited by
- Does opera VPN have kill-switch feature?
- What is the meaning of your IP Adress is unprotected (When i'm using opera VPN, it is appeared)?
-
blackbird71 last edited by
@s91199119 With certain non-Opera VPNs, such a message can appear from the computer's VPN client that simply means you're no longer successfully connected through the VPN's server, hence any Internet connections you make would not be protected/hidden through the VPN and would reveal your normal IP to snooping. I've never heard of that occurring with Opera's VPN client, which is built into the browser itself and, if unable to successfully connect, simply messages that its either trying to connect or is unable to connect to the VPN. Are you instead actually using a VPN extension or a computer-level VPN?
-
A Former User last edited by
i checked security of this VPN through this address (https://torguard.net/whats-my-ip.php) and it showed some information about my current VPN as you see in the image. Maybe they're encouraging us to use their VPN by giving false information. What is the meaning of unprotected?
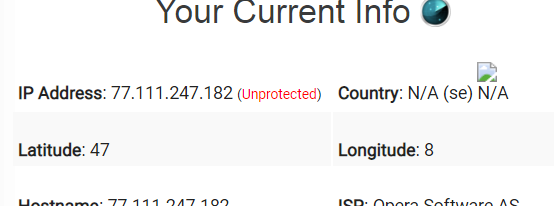
-
A Former User last edited by
Kill Switch is an advanced VPN feature that prevents you from accessing an unprotected Internet connection when your online traffic is not forwarded through VPN. The primary purpose of it is to protect your online activity and IP address from being suddenly exposed in case of a dropped connection from a VPN server.
-
A Former User last edited by
@s91199119
Maybe they're encouraging us to use their VPN by giving false information. What is the meaning of unprotected?
I made the same experience on the website of a VPN provider when I visited it with Opera-VPN activated: In my case as well they claimed that I were "unprotected", which in this context means that they believed to have read my "true" IP address being assigned to me by my Internet Service Provider (and which could be traced back to me personally via my ISP).
However, "my" IP address displayed by this VPN provider was not my own one, but belongs to Opera-VPN.
The IP address displayed on your screenshot is also one of the Opera VPN servers. So you are not unprotected, but the website just does not recognize that a VPN is in use.
-
A Former User last edited by
@s91199119
Does opera VPN have kill-switch feature?
Outside the Opera web browser, Opera VPN does not work. If Opera's currently selected VPN server is unavailable, the blue VPN icon will turn orange/red and website loading will stop until the Opera VPN is available again (or until you select another Opera VPN server that is currently working). This comes close to the function of a kill switch.
For a reliable protection by the Opera VPN you should make sure that
Disable non-proxied UDPis checked in the Opera settings and be aware of third party add-ons which could bypass the VPN. -
blackbird71 last edited by blackbird71
@s91199119 What matters to most VPN users regarding their VPN's exit IP is the (in)accuracy of the IP's purported location in terms of where the user is actually located and the full hiding of their own IP. In order to create a working connection with a website, some kind of 'listed' IP address must be applied to the traffic transiting the VPN's exit server to/from the target website. That listed IP address will tell the Internet traffic relays where to route return traffic so that it finds its way back to the VPN server and then on to the user. In the case of Opera and ordinary VPNs, the 'listed' IP will simply trace back to the directory-listed geolocation of the VPN's exit server and no further.
Hence an Opera VPN user in Tokyo with traffic exiting a VPN server physically located and listed in IP directories as located in Berlin would show up in analysis as having an IP from somewhere roughly within 50 miles or so of Berlin. Analysis of those IP details in a directory-listing would only allow the exit traffic to be traced to an Opera server, which reveals nothing of the actual user. However, it must always be understood (if a user is concerned about the 'location' being accurately traced back to the user's actual location), there are other means for the targeted website only to use WebRTC or site JavaScripting to analyze details from the visiting user's computer during the traffic-stream handshaking to guess more accurately the user's true location. If the traffic stream is encrypted (https), those handshaking details wouldn't, of course, be readable by anyone other than the target website.
Regarding 'kill switches' and the like, apart from @yanta's settings/3rd-party good advice above, this rapidly shifts into the realm of the nature of the traffic one is trying to protect and the personal consequences of its disclosure. For every privacy-protection mechanism, there is a snooping countermeasure of some kind, either real or potential. Each given situation depends on the degree of technical determination on the part of the user and of the censor/snooper. I suggest you read a post I made in another thread here: https://forums.opera.com/post/166732